Manage Software Licenses automatically and accurately.
License compliance doesn’t have to be complex. ONEKEY automatically detects open-source and third-party licenses directly from binary firmware – no source code or manual review needed. Gain full transparency, minimize legal risk, and keep every firmware compliant across its entire lifecycle.

Industry Leaders Rely on ONEKEY
.png)
.png)
.png)



























.png)
.png)
.png)



























.png)
.png)
.png)



























Unseen Licenses Create Costly Liabilities
Undetected open-source components and unclear terms put products and reputations at risk.
Hidden License Risks from Unknown Components
Many teams receive firmware from third parties or suppliers without proper SBOMs or open-source license disclosures. This creates blind spots that can lead to the unintentional use of GPL or non-commercial code – exposing companies to legal and compliance risks. The consequences: license violations, fines, lawsuits, or even forced product withdrawals.
Complex License Combinations and Obligations
Each firmware component can carry multiple licenses with varying requirements – from attribution and modification rights to redistribution limits. When components with conflicting licenses are combined in one product, legal incompatibilities arise that are nearly impossible to detect manually.
Manual and Error-Prone Compliance Checks
Traditional license checks rely on manual mapping, legal reviews, and endless spreadsheets. The process doesn’t scale across large product portfolios and is prone to human error – especially when firmware updates are frequent.
Smart Features for Seamless License Compliance
License Detection from Binary Firmware
ONEKEY automatically extracts licensing information from binary firmware for open-source components, even without access to the source code.
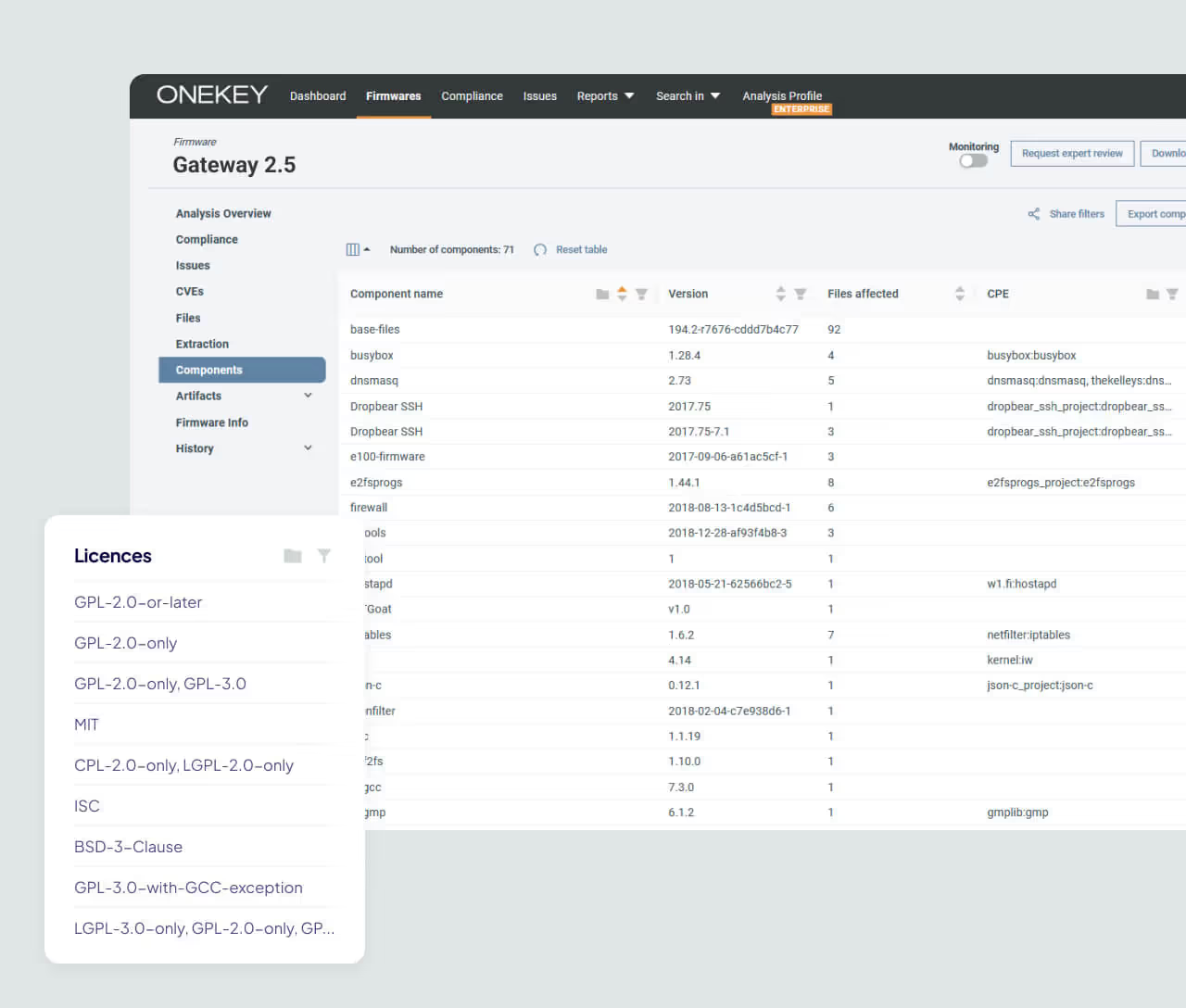
Detailed SBOM with Licensing
Each SBOM includes detailed licensing data for every component, including license names and grouped components per license. This provides full traceability for legal reviews and compliance audits.
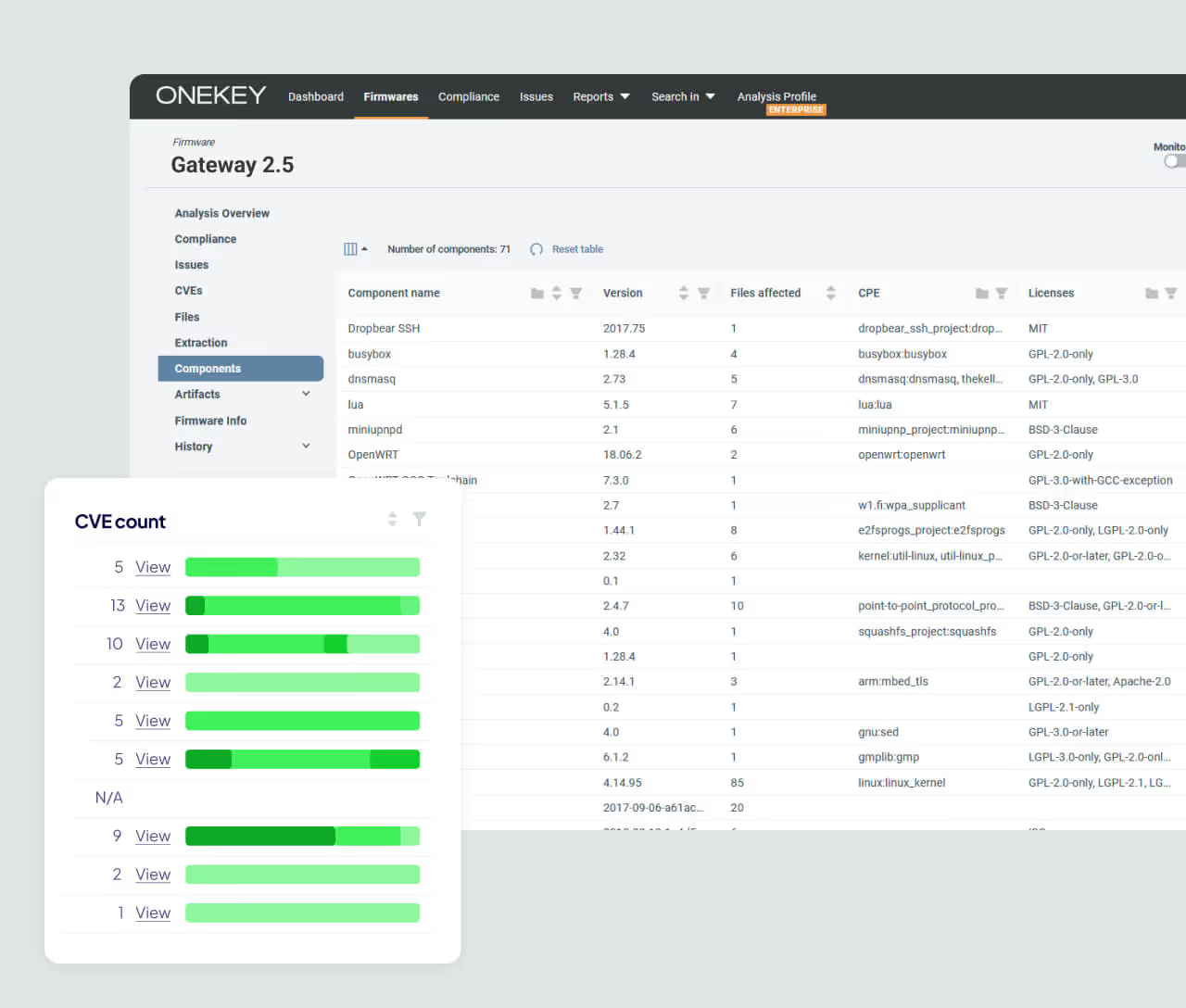
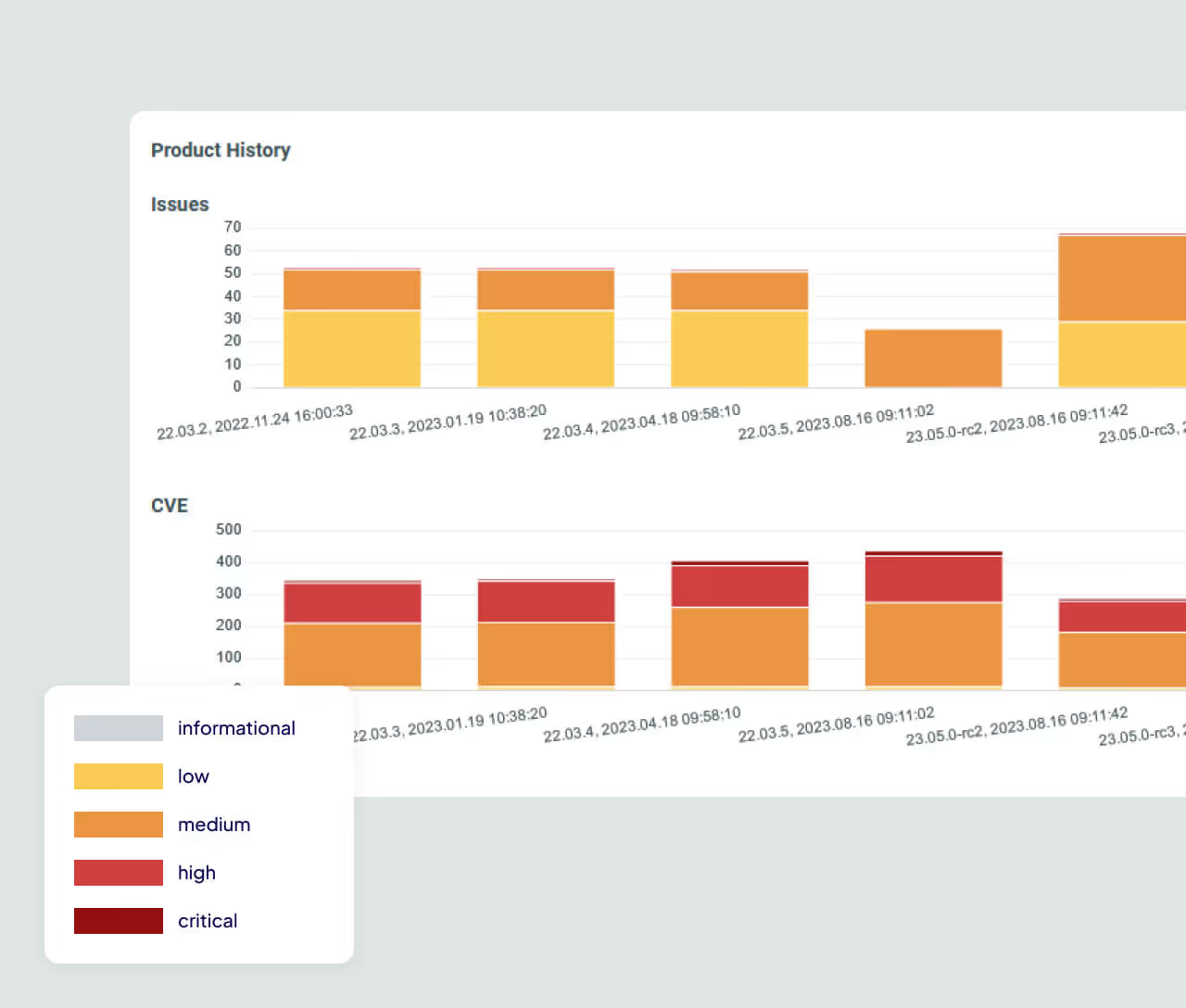
Continuous Monitoring for Licensing Drift
Monitor firmware changes across versions to spot newly added or removed licenses. ONEKEY highlights license shifts and potential policy violations introduced with each update.
Why ONEKEY Redefines Software License Compliance
ONEKEY enables organizations to ensure compliance, uncover hidden obligations, and prevent costly license violations – all with zero manual effort.
Minimize Legal Risk
Identify unknown or non-compliant licenses early to prevent IP violations, product recalls, or lawsuits. ONEKEY helps uncover legal risks hidden deep within firmware binaries – before they become a problem.
Automate License Detection Workflows
Manual license checks for every firmware are slow and tedious. ONEKEY automatically identifies license types, flags risky ones, and streamlines collaboration between legal and security teams – faster, easier, and with less overhead.
Stay Continuously Compliant
As firmware evolves, licenses change too. ONEKEY ensures continuous compliance across every firmware version – even for long-life devices in complex, regulated industries.
FACTS & Figures
FACTS & Figures
100% Visibility into Third-Party Open-source License use
90% Less Time Spent on Manual License Checks
30+ Workdays saved Per Year For Licensing Reviews
Automate License Compliance with ONEKEY
Turn complex license management into a seamless process. ONEKEY empowers your team to stay compliant, reduce effort, and prevent costly violations.
Why Customers Trust Us
FAQs
Get detailed answers to the most common questions on safeguarding your connected products.

What is Product Cybersecurity?
Product cybersecurity ensures your digital products—whether software, hardware, or connected devices—are protected against cyber threats throughout their entire lifecycle. From design to deployment and beyond, robust cybersecurity practices safeguard against data breaches, unauthorized access, and cyberattacks. This proactive approach not only secures the product but also ensures compliance with evolving regulations, reducing risks and maintaining the integrity and trustworthiness of your technology.
Why is Product Cybersecurity Important?
Product cybersecurity is essential to protect your digital products from cyber threats, safeguarding sensitive data and ensuring seamless operation. Without it, your products and users are at risk of attacks, data breaches, and unauthorized access that can result in costly financial losses, reputational damage, and compromised safety. Strong cybersecurity practices help you stay compliant with regulations, build customer trust, and keep your products resilient against evolving cyber threats.
How do you ensure product cybersecurity?
Securing your products requires a strategic and continuous approach throughout their entire lifecycle. Here’s how you can achieve it:
- Conduct Security Audits & Assessments: Regularly evaluate your products to uncover and fix vulnerabilities before they become threats.
- Manage Vulnerabilities Effectively: Leverage SBOMs, VEX, and automated tools to track, assess, and mitigate risks.
- Stay Updated: Keep your products secure by applying patches and updates to defend against the latest cyber threats.
- Ensure Compliance: Meet all relevant security standards and regulations to avoid legal risks and maintain customer trust.
Build. Comply. Resist. Repeat. With these steps, you’ll stay ahead of the curve and keep your products and customers secure.
What is an SBOM used for?
An SBOM (Software Bill of Materials) gives you a complete overview of all components in your software. It’s key for managing vulnerabilities, sharing information, ensuring license compliance, and maintaining transparency across your supply chain. With an SBOM, you gain the visibility you need to keep your products secure and compliant—every step of the way.
What is a Digital Cyber Twin?
A Digital Cyber Twin is a virtual replica of your product’s digital ecosystem. It lets you test and analyze your system in a safe, simulated environment—detecting vulnerabilities and optimizing security before they can impact your real-world product. It’s like having a crystal ball for your cybersecurity, helping you stay ahead of potential threats without risking your actual systems.





