Automate Red Team Testing at Scale
Red teams go beyond theory – they simulate real-world attacks to expose weaknesses before attackers can exploit them. By probing firmware, products, and connected systems, they reveal exploitable vulnerabilities, validate security controls, and strengthen product resilience. They uncover what really matters and turn potential blind spots into actionable insights.

Industry Leaders Rely on ONEKEY
.png)
.png)
.png)



























.png)
.png)
.png)



























.png)
.png)
.png)



























Red Team Testing
Faces a Speed Gap
Manual reverse-engineering, endless triage, and thousands of CVEs slow teams down — making it harder to focus on the real, exploitable risks.
Time-consuming Manual Firmware Analysis
Red Teams waste days or even weeks manually reverse-engineering complex firmware. Without the right tools, every dependency must be mapped by hand, every vulnerability traced manually. This results in slow, resource-heavy workflows that delay detection and testing.
Vulnerability Overload Without Context
Red Teams are flooded with hundreds or thousands of CVEs per firmware. Without exploitability context, they waste valuable time chasing low-risk or already mitigated issues. This causes weaker attack simulations and delayed insights for stakeholders.
Falling Behind on Firmware Updates
Constant firmware updates, patches, and versions introduce new vulnerabilities or reintroduce old ones, making it hard for Red Teams to stay up to date. Without visibility into how each version evolves, they risk working with outdated information or missing exploitable weaknesses. This forces manual re-analysis with every update – a time-consuming, resource-heavy process that slows testing depth and limits effectiveness in fast-moving engagements.
Focused Features for Faster Red Team Testing
60% Fewer False Positives. Real Results.
Instead of flagging every CVE, ONEKEY evaluates vulnerabilities in the real firmware context. When new vulnerabilities are disclosed, the platform instantly checks whether the firmware is affected – cutting noise and removing manual effort. The result: over 60% fewer false positives, validation reduced from days to minutes, and red teams focused only on real attack vectors.

Binary-Level Vulnerability Detection
ONEKEY analyzes the firmware binaries directly without source code, generating a detailed SBOM and uncovering vulnerabilities. This enables red teams to skip manual reverse-engineering and move straight to exploiting real risks.
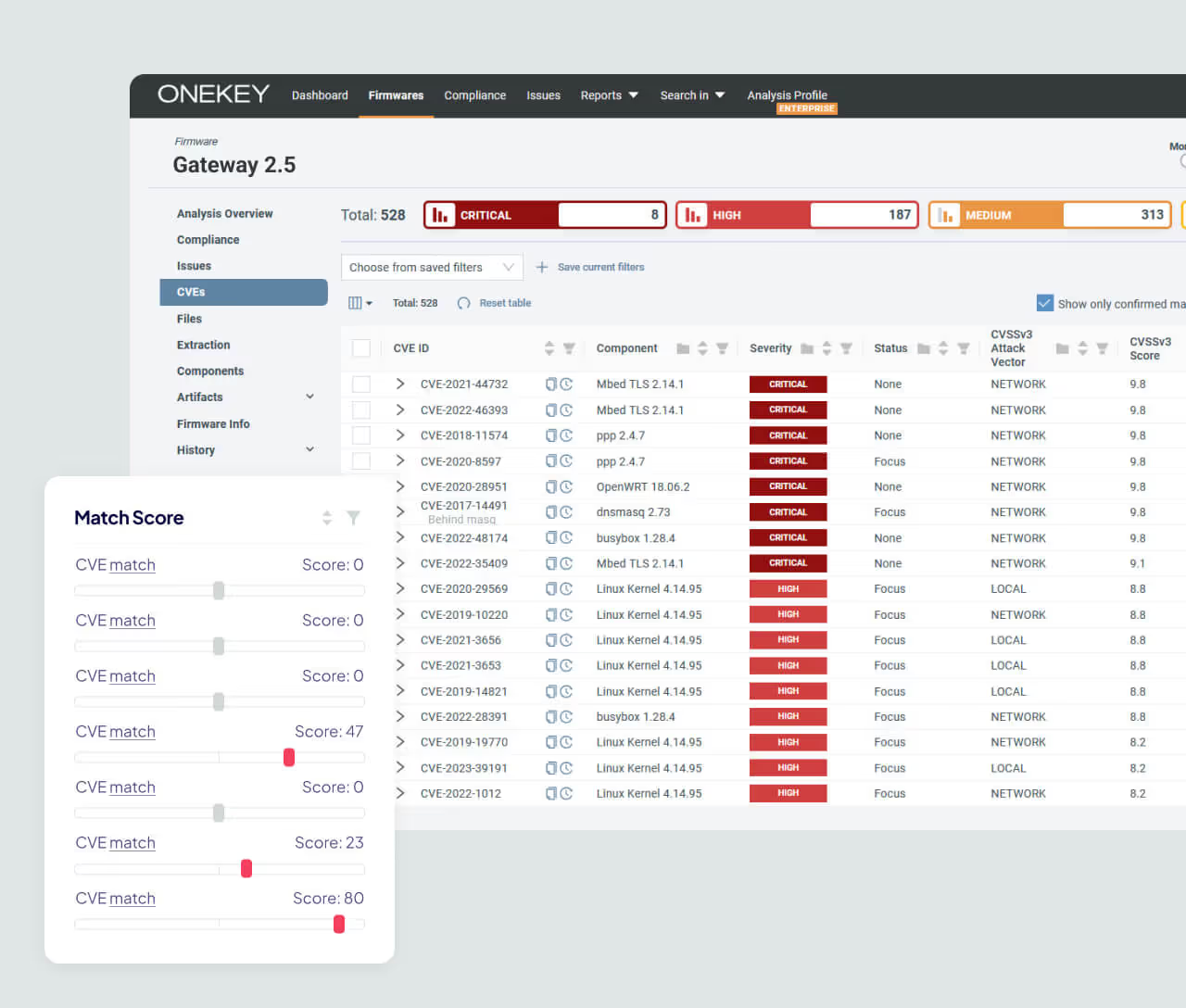
Continuous Firmware Monitoring
ONEKEY continuously monitors firmware across versions and product lines. The platform tracks every change introduced in new updates and flags security-relevant differences – from reintroduced vulnerabilities to unsafe configurations or newly exploitable components. Red teams no longer start from scratch; they get version-aware insights that show what’s new, what’s fixed, and where the next attack opportunities lie. This accelerates discovery and keeps testing focused on the most relevant, high-risk targets.
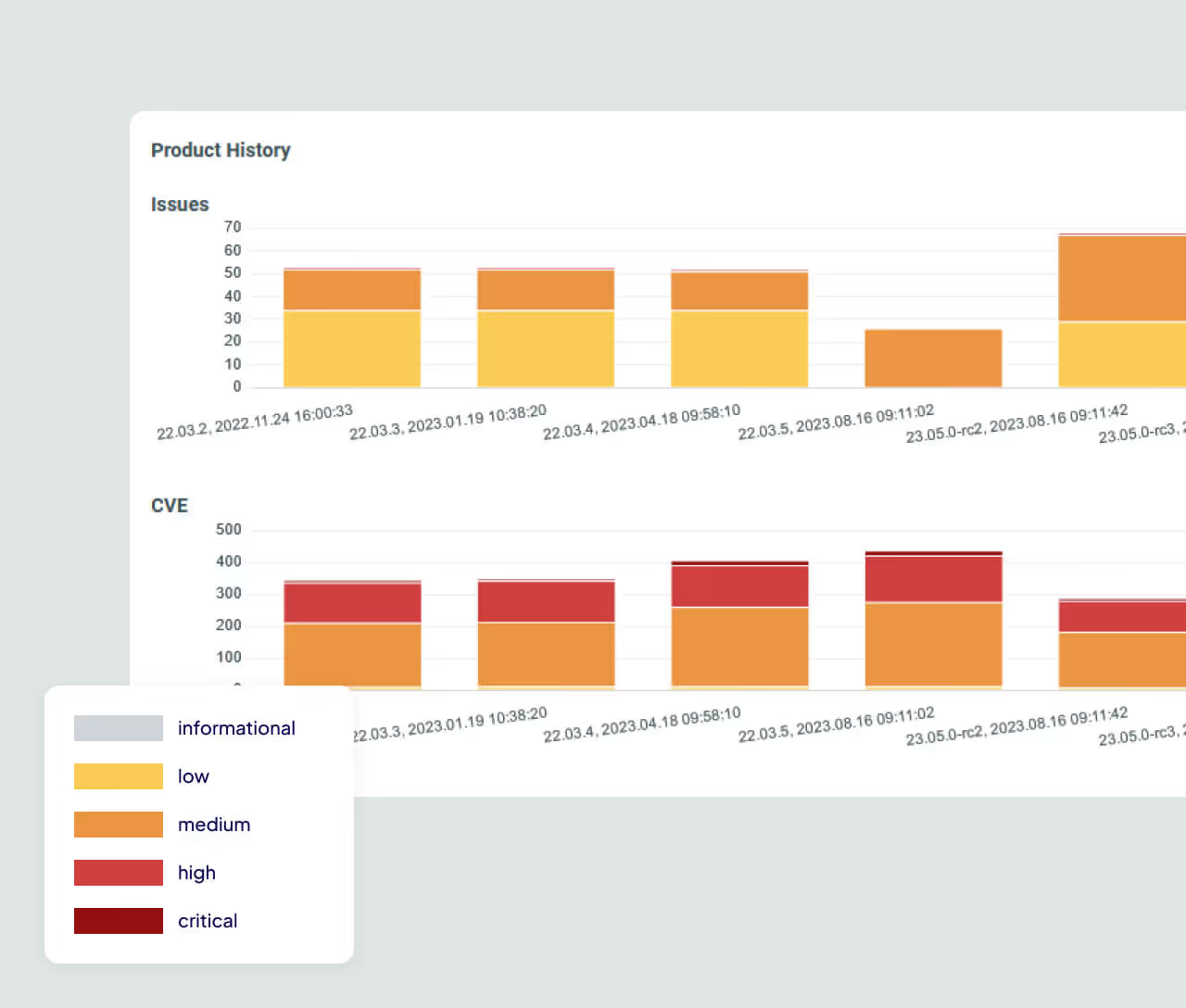
Why ONEKEY Transforms Red Team Automation
Discover how automation accelerates testing, eliminates false positives, and empowers teams to focus on exploitable risks that truly matter.
Discover Real Vulnerabilities Faster
ONEKEY’s binary-level analysis finds exploitable vulnerabilities in minutes, not days. It filters out irrelevant issues, highlights real risks, and keeps red teams focused on what matters – enabling faster testing, sharper insights, and stronger results.
Maximize Testing Efficiency
Red teams don’t need raw data – they need clarity. ONEKEY highlights exploitable vulnerabilities based on firmware usage and configuration, cutting through noise. Focus less on manual triage and more on real-world attack scenarios.
Reduce Cost, Deliver Faster
Manual red team work burns weeks before testing even begins. ONEKEY automates binary analysis, cutting prep time while keeping deep accuracy. Teams achieve faster results at lower cost – making continuous assessments finally realistic.
FACTS & Figures
FACTS & Figures
4x Faster
Vulnerability Discovery
Automated binary-level analysis cuts detection time dramatically and surfaces high-risk issues in minutes.
60 % Fewer False Positives
ONEKEY’s context-aware filtering focuses on exploitable risks — red teams work smarter, not harder.
10x Broader Attack Coverage Continuous firmware monitoring across versions enables a deeper testing scope with fewer manual efforts.
Accelerate Red Team Testing – Without the Manual Bottlenecks
Uncover exploitable vulnerabilities in minutes, cut false positives, and focus only on real attack paths.
Why Customers Trust Us
Real Attack Simulation. Automated with Confidence.
Simulate real-world exploits faster and smarter with ONEKEY’s automated red team capabilities.

Respond Fast to Critical Threats
Identify critical vulnerabilities with ONEKEY's automated zero-day analysis. Improve response time for IoT/OT with precise, centralized monitoring.

Tailor Your Threat Models
Unlock customized threat modeling with Custom Analysis Profiles. Integrate personalized rules, prioritize CVEs, and define risk levels for your business.

Unified SBOM Generation and Normalization
ONEKEY automatically creates complete, accurate SBOMs directly from binary firmware — no source code or supplier data needed. The platform consolidates and standardizes multiple SBOMs into one unified view across all products and versions, eliminating inconsistencies and blind spots. Security teams gain full visibility, reliable vulnerability tracking, and confidence that no critical component is missed.
FAQs
Get detailed answers to the most common questions on safeguarding your connected products.

What is Product Cybersecurity?
Product cybersecurity ensures your digital products—whether software, hardware, or connected devices—are protected against cyber threats throughout their entire lifecycle. From design to deployment and beyond, robust cybersecurity practices safeguard against data breaches, unauthorized access, and cyberattacks. This proactive approach not only secures the product but also ensures compliance with evolving regulations, reducing risks and maintaining the integrity and trustworthiness of your technology.
Why is Product Cybersecurity Important?
Product cybersecurity is essential to protect your digital products from cyber threats, safeguarding sensitive data and ensuring seamless operation. Without it, your products and users are at risk of attacks, data breaches, and unauthorized access that can result in costly financial losses, reputational damage, and compromised safety. Strong cybersecurity practices help you stay compliant with regulations, build customer trust, and keep your products resilient against evolving cyber threats.
How do you ensure product cybersecurity?
Securing your products requires a strategic and continuous approach throughout their entire lifecycle. Here’s how you can achieve it:
- Conduct Security Audits & Assessments: Regularly evaluate your products to uncover and fix vulnerabilities before they become threats.
- Manage Vulnerabilities Effectively: Leverage SBOMs, VEX, and automated tools to track, assess, and mitigate risks.
- Stay Updated: Keep your products secure by applying patches and updates to defend against the latest cyber threats.
- Ensure Compliance: Meet all relevant security standards and regulations to avoid legal risks and maintain customer trust.
Build. Comply. Resist. Repeat. With these steps, you’ll stay ahead of the curve and keep your products and customers secure.
What is an SBOM used for?
An SBOM (Software Bill of Materials) gives you a complete overview of all components in your software. It’s key for managing vulnerabilities, sharing information, ensuring license compliance, and maintaining transparency across your supply chain. With an SBOM, you gain the visibility you need to keep your products secure and compliant—every step of the way.
What is a Digital Cyber Twin?
A Digital Cyber Twin is a virtual replica of your product’s digital ecosystem. It lets you test and analyze your system in a safe, simulated environment—detecting vulnerabilities and optimizing security before they can impact your real-world product. It’s like having a crystal ball for your cybersecurity, helping you stay ahead of potential threats without risking your actual systems.







