Compliance Management for Embedded Firmware
Ensure your products meet evolving cybersecurity regulations, standards, and internal policies – from EU CRA and IEC 62443 to RED and NIS2. ONEKEY automates compliance validation, evidence generation, and continuous monitoring, helping organizations replace manual checklists with scalable, audit-ready workflows.

Industry Leaders Rely on ONEKEY
.png)
.png)
.png)



























.png)
.png)
.png)



























.png)
.png)
.png)



























Evolving Regulations Create Compliance Complexity
Constantly changing cybersecurity standards, overlapping requirements, and manual audit processes make it nearly impossible to maintain continuous compliance. Without automation and visibility, compliance gaps, hidden risks, and regulatory drift emerge across firmware versions and product lines.
Navigating Constantly Evolving Regulations
Security and compliance frameworks such as EU CRA, IEC 62443, RED, or NIS2 evolve faster than most teams can adapt. For organizations managing multiple embedded products and firmware versions, staying aligned with every new provision is complex and time-consuming. Manual tracking across spreadsheets and departments often leads to outdated requirements, inconsistent documentation, and delayed compliance actions.
Lack of Audit Readiness
Preparing for internal or external audits requires complete, verifiable evidence – from SBOMs and vulnerability reports to proof of compliance. Without integrated systems, teams spend excessive time compiling data from different sources, often ending up with inconsistent or incomplete records. The result: delayed certifications, higher audit costs, and increased compliance risk.
Fragmented Visibility Across Teams and Versions
Compliance gaps often remain hidden within siloed departments or firmware releases. Without a centralized overview, organizations lack clarity on which requirements are unmet, which products are affected, and how to prioritize remediation. This fragmentation leads to blind spots, delayed corrective actions, and increased risk of non-conformity.
Smart Features for Continuous Compliance Management
ONEKEY automates every step of firmware compliance – from regulatory mapping and SBOM generation to continuous monitoring and audit preparation. With guided workflows, evidence generation, and change tracking, teams can ensure that every product version stays compliant with evolving standards like EU CRA, IEC 62443, and RED – without manual overhead.
End-to-End Regulatory Alignment
ONEKEY’s Compliance Wizard guides organizations through global standards such as the EU CRA, UN Regulation R155, RED, IEC 62443, and ETSI EN 303 645. For each requirement, it shows whether it’s met, violated, needs manual validation, or is not applicable – even as regulations evolve or differ across product lines. Users can generate audit-ready compliance bundles in PDF, JSON, or CSV, complete with evidence, vulnerability details, and SBOMs. This drastically cuts manual effort and keeps teams always ready for audits or certifications.
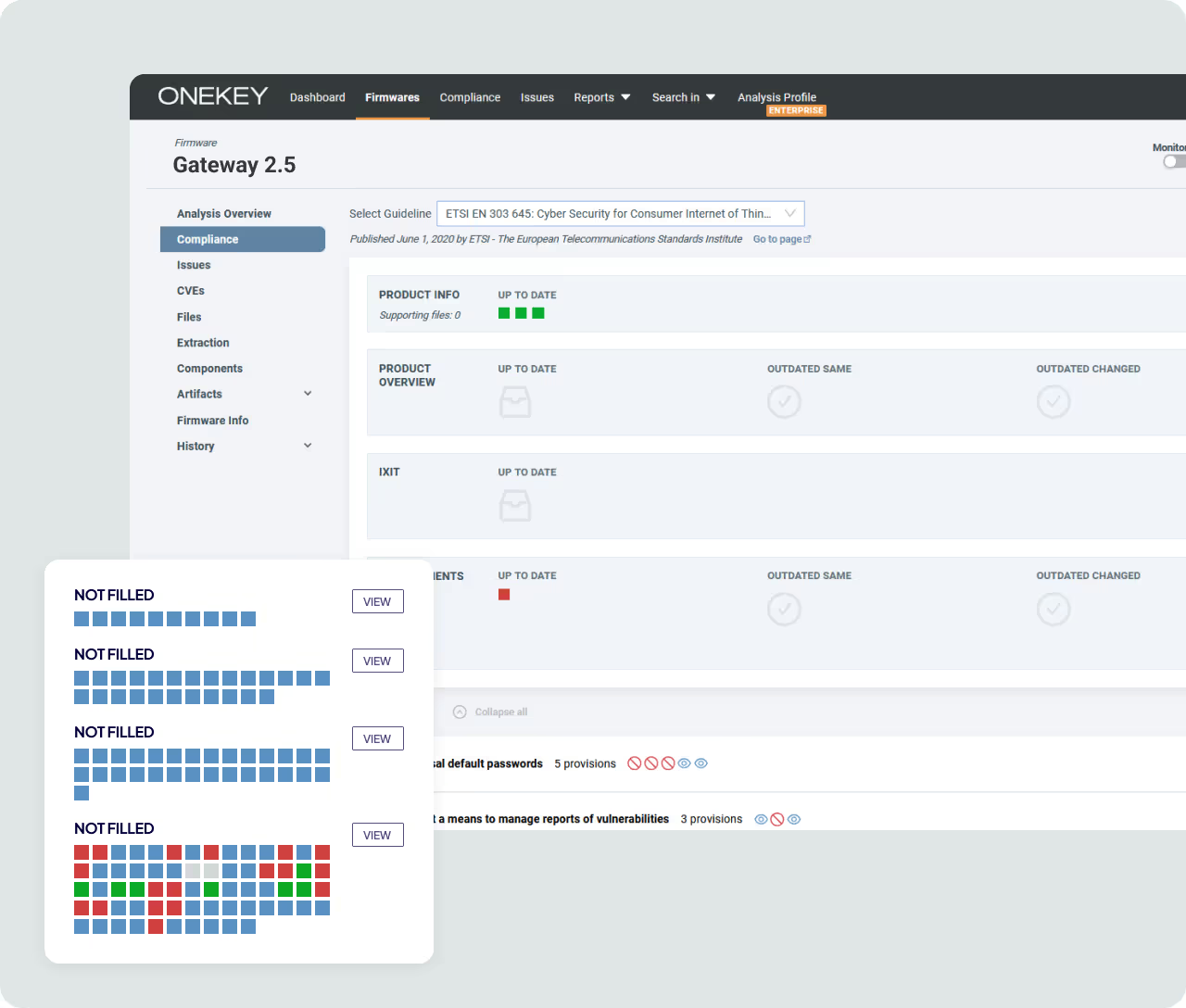
SBOM Management as Foundation of Compliance
Accurate compliance starts with visibility. ONEKEY automatically generates SBOMs directly from binary firmware – even without source code. Every open-source, third-party, and proprietary component is identified and cataloged. With standardized SBOM formats, organizations can align with regulatory expectations and eliminate blind spots in their component inventory.
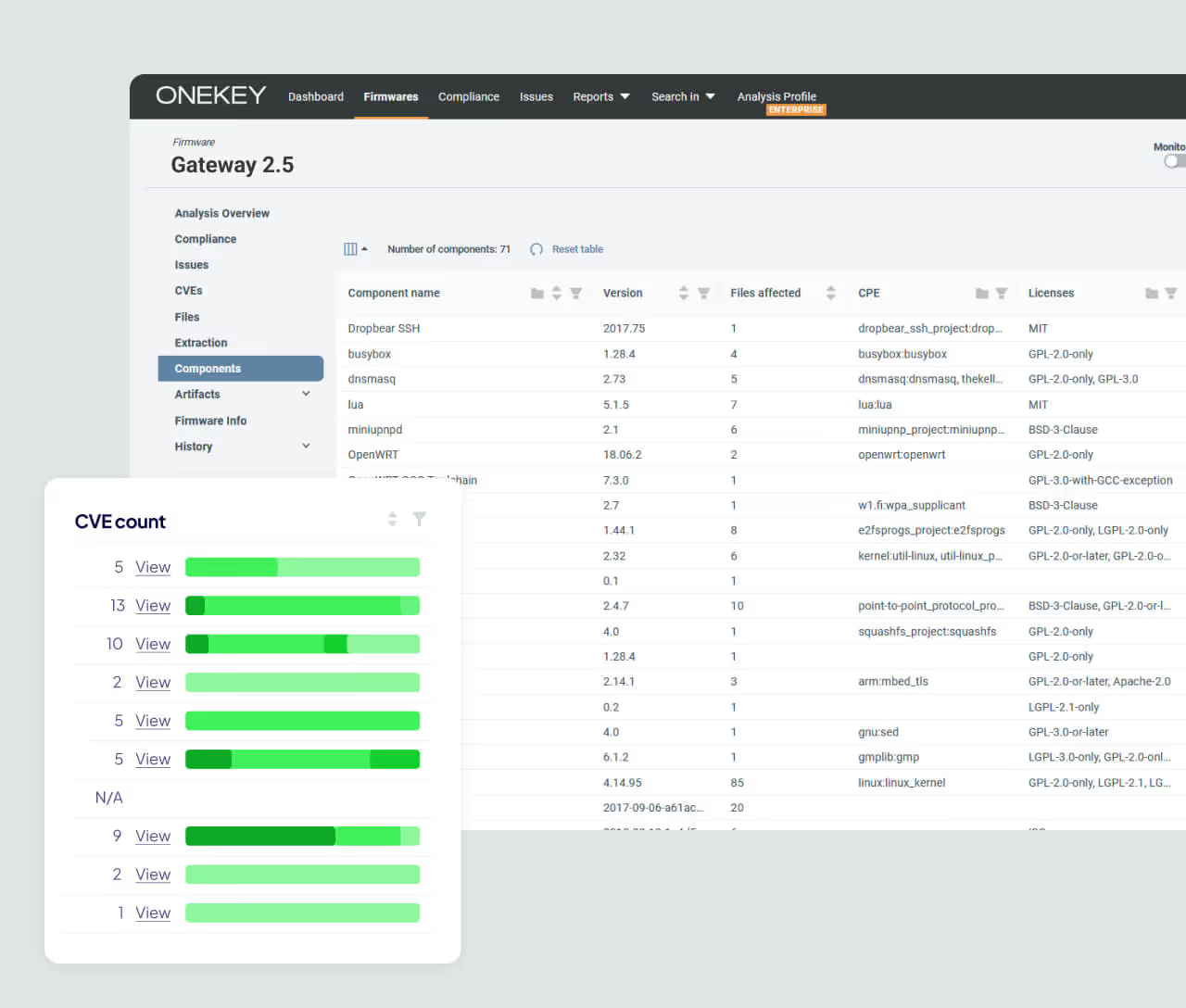
Stay Compliant Over Time
Compliance is never “one and done.” Firmware updates, new vulnerabilities, and evolving standards can quietly cause compliance drift. ONEKEY’s monitoring continuously tracks firmware changes and flags affected provisions – ensuring compliance stays consistent over time.
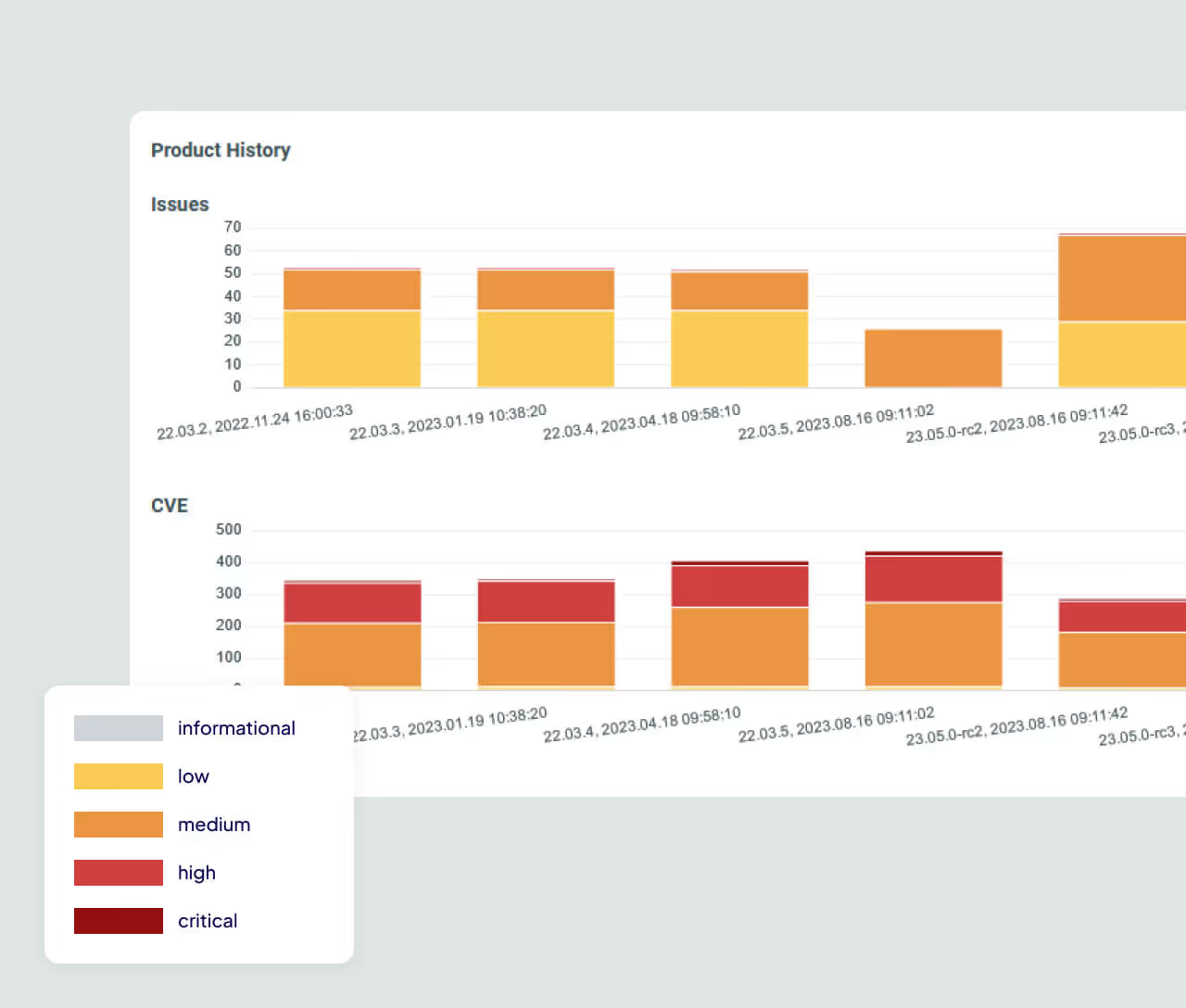
Why ONEKEY Redefines Compliance Management
ONEKEY transforms compliance from a manual, reactive process into an automated, scalable workflow. By analyzing firmware at binary level, it maps regulatory requirements, detects compliance gaps, and generates audit-ready evidence automatically. The result: continuous compliance, reduced audit effort, and full confidence in meeting global cybersecurity standards.
Reduced Legal and Regulatory Risk
By identifying compliance gaps early, ONEKEY helps organizations prevent costly penalties, product recalls, and market delays. Automated license and standards validation ensures every firmware release meets evolving cybersecurity and regulatory requirements – minimizing exposure and protecting brand reputation.
Faster Time to Audit and Certification
With ONEKEY’s automated compliance workflows, organizations can generate complete, audit-ready reports in minutes instead of hours. This accelerates certification processes, shortens time to market, and frees teams from repetitive manual documentation tasks.
Resilience Against Regulatory Drift
Continuous monitoring ensures compliance doesn’t erode over time. ONEKEY tracks firmware updates, vulnerabilities, and component changes to automatically detect when a previously compliant product falls out of specification – enabling proactive action before audits or releases.
FACTS & Figures
FACTS & Figures
ONEKEY automates every step of firmware compliance – from regulatory mapping and SBOM generation to continuous monitoring and audit preparation. With guided workflows, evidence generation, and change tracking, teams can ensure that every product version stays compliant with evolving standards like EU CRA, IEC 62443, and RED – without manual overhead.
Save 80% of Audit Preparation Time
Detect Compliance Gaps 70% Earlier
Scale Compliance Oversight by 3x Without Extra Headcount
Achieve Continuous Compliance with ONEKEY
Replace manual spreadsheets and fragmented audits with automated, scalable workflows. ONEKEY helps your teams meet regulatory requirements faster, stay aligned with global standards, and prevent compliance drift before it happens.
Why Customers Trust Us
FAQs
Get detailed answers to the most common questions on safeguarding your connected products.

What is Product Cybersecurity?
Product cybersecurity ensures your digital products—whether software, hardware, or connected devices—are protected against cyber threats throughout their entire lifecycle. From design to deployment and beyond, robust cybersecurity practices safeguard against data breaches, unauthorized access, and cyberattacks. This proactive approach not only secures the product but also ensures compliance with evolving regulations, reducing risks and maintaining the integrity and trustworthiness of your technology.
Why is Product Cybersecurity Important?
Product cybersecurity is essential to protect your digital products from cyber threats, safeguarding sensitive data and ensuring seamless operation. Without it, your products and users are at risk of attacks, data breaches, and unauthorized access that can result in costly financial losses, reputational damage, and compromised safety. Strong cybersecurity practices help you stay compliant with regulations, build customer trust, and keep your products resilient against evolving cyber threats.
How do you ensure product cybersecurity?
Securing your products requires a strategic and continuous approach throughout their entire lifecycle. Here’s how you can achieve it:
- Conduct Security Audits & Assessments: Regularly evaluate your products to uncover and fix vulnerabilities before they become threats.
- Manage Vulnerabilities Effectively: Leverage SBOMs, VEX, and automated tools to track, assess, and mitigate risks.
- Stay Updated: Keep your products secure by applying patches and updates to defend against the latest cyber threats.
- Ensure Compliance: Meet all relevant security standards and regulations to avoid legal risks and maintain customer trust.
Build. Comply. Resist. Repeat. With these steps, you’ll stay ahead of the curve and keep your products and customers secure.
What is an SBOM used for?
An SBOM (Software Bill of Materials) gives you a complete overview of all components in your software. It’s key for managing vulnerabilities, sharing information, ensuring license compliance, and maintaining transparency across your supply chain. With an SBOM, you gain the visibility you need to keep your products secure and compliant—every step of the way.
What is a Digital Cyber Twin?
A Digital Cyber Twin is a virtual replica of your product’s digital ecosystem. It lets you test and analyze your system in a safe, simulated environment—detecting vulnerabilities and optimizing security before they can impact your real-world product. It’s like having a crystal ball for your cybersecurity, helping you stay ahead of potential threats without risking your actual systems.







