PENETRATION TESTING WITH ONEKEY
We uncover vulnerabilities—before others can exploit them.
At ONEKEY, we go beyond surface-level testing. Our penetration testing services target what really matters: critical infrastructure, enterprise IT, cloud environments, applications, and—most importantly—hardware. With proven methods and real-world expertise, we deliver clarity where others stop at checklists.

With ONEKEY, you identify and fix vulnerabilities before they become real problems.
Stay Ahead of Evolving Threats with Early, Expert-Driven Security
Risk Identification
Uncover security gaps across hardware, software, and networks—before attackers do.
Actionable Recommendations
Receive prioritized, detailed guidance tailored to your specific environment.
Regulatory Compliance
Meet industry standards like IEC 62443 and align with evolving compliance needs.
Operational Peace of Mind
Reduce the risk of downtime, data loss, and reputational damage through proactive testing.

WHY PENETRATION TESTING MATTERS
Hardware Penetration Testing fOr OT & IOT
Software testing isn’t enough. We secure what others can’t even see.
Operational Technology (OT) & Industrial Control Systems (ICS)
We identify security gaps in programmable logic controllers (PLCs), SCADA systems, and other mission-critical components—before attackers do.
IoT Devices
Whether it's a connected thermostat or a complex sensor network—we analyze how devices communicate, store data, and manage access.
Embedded Systems
We dig into firmware, hardware interfaces, and software stacks to expose deep-seated vulnerabilities others miss.
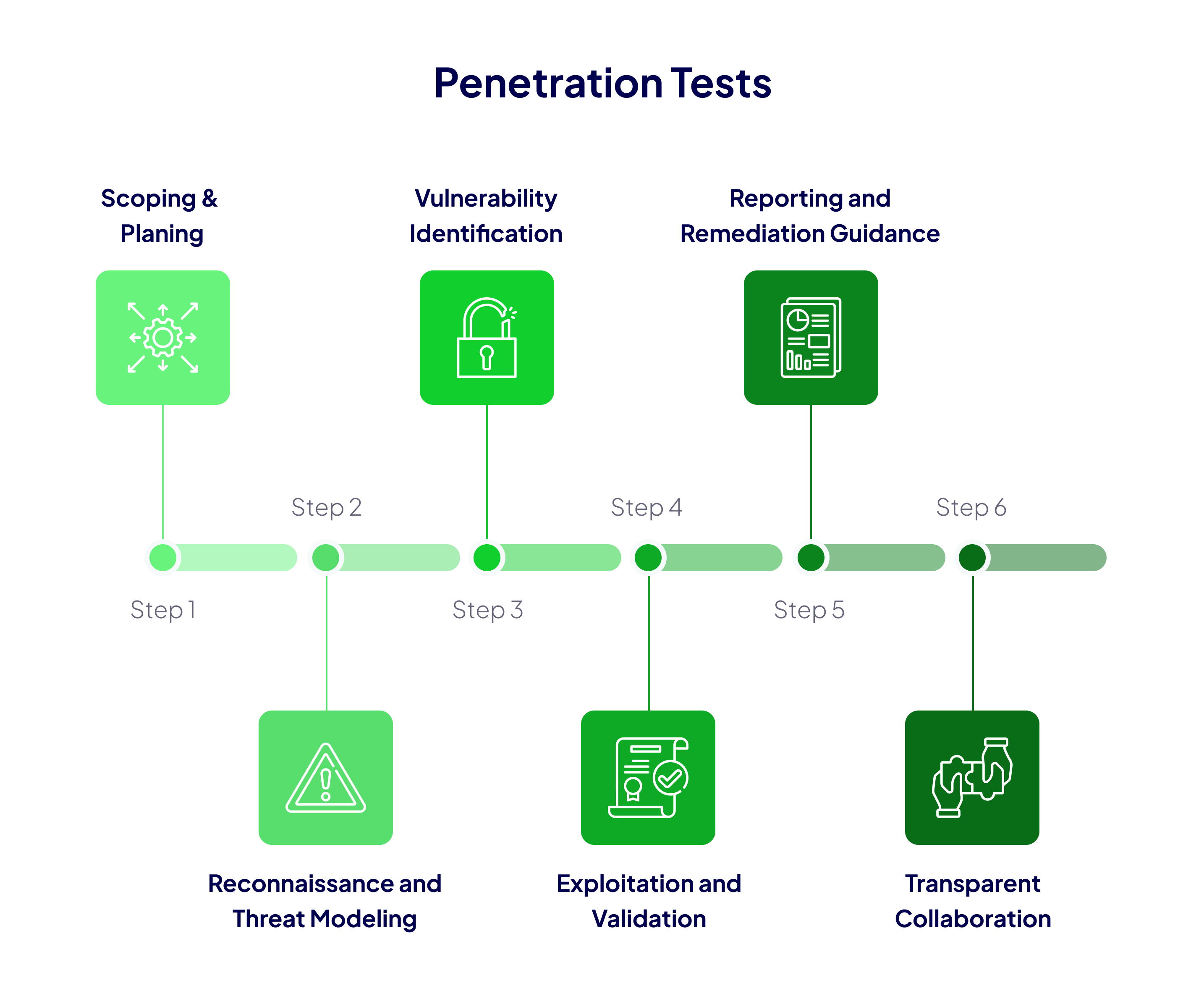
Our Penetration Testing Approach
We work closely with you to define testing goals, target systems, and success criteria. This ensures each test is custom-tailored to your specific needs
Our specialists investigate available documentation, device architectures, and potential attack surfaces, forming a detailed threat model that guides the penetration test.
Using manual techniques, industry-standard tools, and our ONEKEY platform, we methodically analyze hardware interfaces, firmware, network interactions, and software components.
We attempt to exploit identified vulnerabilities—always in a controlled manner—to validate their severity and potential impact. This hands-on approach ensures accurate risk assessments.
Our final deliverable includes comprehensive technical documentation, management-friendly summaries, and detailed remediation steps that help you address each discovered vulnerability effectively.
We maintain open lines of communication throughout the testing process, ensuring you remain informed and in control.

Benefits of Partnering with ONEKEY
Deep Hardware Expertise: Our engineers and researchers have extensive experience with OT, IoT, and embedded systems.
Advanced Tools & Platforms: We utilize our ONEKEY firmware analysis platform to work faster and more efficiently than traditional manual-only methods.
Customized Engagements: Every environment is unique. We adapt our process and scope to meet your exact operational, compliance, and security needs.
Transparent Collaboration: We maintain open lines of communication throughout the testing process, ensuring you remain informed and in control.
Ready to Strengthen Your Defenses?
Protect your devices, data, and operations with expert-level penetration testing.
Let’s make your infrastructure secure—together.