Advisory: Multiple issues in Realtek SDK affect hundreds of thousands of devices down the supply chain

At least 65 vendors affected by severe vulnerabilities that enable unauthenticated attackers to fully compromise the target device and execute arbitrary code with the highest level of privilege.
Overview
Over the course of a research project focusing on a specific cable modem, we identified that the system was using a dual-SoC design. The main SoC was running a Linux system, while the second SoC – a dedicated Realtek RTL819xD chipset implementing all the access point functions – was found to be running another, stripped-down Linux system from Realtek.
Realtek chipsets are found in many embedded devices in the IoT space. RTL8xxx SoCs – which provide wireless capabilities – are very common. We therefore decided to spend time identifying binaries running on the RTL819xD on our target device, which expose services over the network and are provided by Realtek themselves. Such binaries are packaged as part of the Realtek SDK, which is developed by Realtek and provided to vendors and manufacturers who use the RTL8xxx SoCs.
Supported by IoT Inspector’s firmware analysis platform, we performed vulnerability research on those binaries and identified more than a dozen vulnerabilities – ranging from command injection to memory corruption affecting UPnP, HTTP (management web interface), and a custom network service from Realtek.By exploiting these vulnerabilities, remote unauthenticated attackers can fully compromise the target device and execute arbitrary code with the highest level of privilege.
We identified at least 65 different affected vendors with close to 200 unique fingerprints, thanks both to Shodan’s scanning capabilities and some misconfiguration by vendors and manufacturers who expose those devices to the Internet. Affected devices implement wireless capabilities and cover a wide spectrum of use cases: from residential gateways, travel routers, Wi-Fi repeaters, IP cameras to smart lightning gateways or even connected toys.
Key Takeaways
As awareness for supply chain transparency is on the rise among security experts, this example is a pretty good showcase of the vast implications of an obscure IoT supply chain. As opposed to recent supply chain attacks such as Kaseya or Solar Winds, where perpetrators went to great lengths to infiltrate the vendor’s release processes and place hidden backdoors in product updates, this example is far less sophisticated – and probably way more common, for three simple reasons:
- On the supplier’s end, insufficient secure software development practices, in particular lack of security testing and code review, resulted in dozens of critical security issues to remain untouched in Realtek’s codebase for more than a decade (from 2.x branch through “Jungle“ SDK to “Luna” SDK).
- On the product vendor’s end, we see manufacturers with access to the Realtek source code (a requirement to build Realtek SDK binaries for their own platform) who missed to sufficiently validate their supply chain, left the issues unspotted and distributed the vulnerabilities to hundreds of thousands of end customers – leaving them vulnerable to attacks.
- But supply chain issues can go upstream, too. During our research, we discovered that security researchers and pen-testers have previously identified issues in devices relying on the Realtek SDK, but didn’t link these issues to Realtek directly. Vendors who received reports of these vulnerabilities fixed them in their own branch but did not notify Realtek, leaving others exposed.
Our firmware analysis platform IoT Inspector can support in detecting such crucial supply chain issues. It automatically detects whether a firmware is based on a vulnerable Realtek SDK, along with its specific version. It can also detect each vulnerability we reported, and whether or not the provided patch has been applied.
Please keep reading for the full details of our research process.
UPnP Vulnerabilities (mini_upnpd, wscd)
Summary
Realtek moved away from its previous UPnP service miniigd in response to CVE-2014-8361, They subsequently provided the source to build two binaries with different features within its SDK:
- mini_upnpd: seems to be only handling SSDP packets and does not expose a UPnP HTTP interface. For every firmware image we identified to contain a mini_upnpd binary, wscd was also present.
- wscd: aka ‘Realtek WiFi Simple-Config Daemon’, implements both SSDP packet handling and a UPnP HTTP interface.
Throwing the right keywords into Google, we were able to get access to the source code on Github. This helped in speeding up the vulnerability identification – but we’re confident that skilled reverse engineers would reach the same conclusions, given that some binaries in our sample set came with debug symbols. To illustrate the vulnerabilities, we have commented relevant sections of the source code.
Stack Buffer Overflow via UPnP SUBSCRIBE Callback Header
A few words on UPnP subscription
Any UPnP service must expose the list of devices that it manages, as well as a list of services attached to those devices. In the sample below taken from gupnp documentation (Writing a UPnP Service: GUPnP Reference Manual ), we see a virtual light device with a power switching service attached to it.
On line 19, we can see a eventSubURL item that is related to a feature of UPnP: event notification.
To subscribe to event notification for a service, a subscriber shall send a request with method SUBSCRIBE, alongside populated NT and CALLBACK header fields, to that service’s fully-qualified event subscription URL.
An UPnP SUBSCRIBE request usually looks like this:
On events, the UPnP service will then notify the subscriber by sending a NOTIFY request to the provided CALLBACK URL. In our example, an event could be the virtual light being switched on or off by another UPnP client.
Now that you have some background on UPnP event notifications and subscriptions, let’s look into the Realtek SDK implementation.
Whenever a request is received by the UPnP handler, the HTTP verb is checked and a dedicated function called:
On line 8, the UPnPProcessSUBSCRIBE function will parse the HTTP request held in a upnphttp structure and fill the fields of the provided process_upnp_subscription structure:
The ParseSUBSCRIBEPacket function parses the HTTP request line. It first validates that the URL is a valid event URL (line 21 to 29), checks that the host header corresponds to its own IP and port (line 41 to 53), and finally extracts the IP and port number from the callback header value by calling GetIPandPortandCallBack on line 59:
The GetIPandPortandCallback function is represented below so that you can try to find the vulnerability yourself. We provide a detailed explanation below.
GetIPandPortandCallBack parsing code is wrong on many levels, but let’s focus on why it’s vulnerable:
- it checks whether the Callback starts with
"<http://"and bails otherwise from line 12 to 21.
From line 26 to 67, the actual IP and port number extraction starts:
- it will advance in the buffer until a ‘:’ or a ‘/’ is found, every time a ‘.’ is encountered, a counter is incremented
- when there is a hit for ‘:’ or ‘/’, it checks if there are 3 dots (strong validation for IPv4, right ?)
- if the character hit is ‘/’, it defaults to port number 80
- if the character hit is ‘:’, it continues reading the buffer until they hit a ‘/’ character and copy the buffer from ‘:’ to ‘/’ into a fixed size buffer named ‘port’
- the port buffer is then fed to
atoito get an integer
The vulnerability happens on line 58 where memcpy is called with a length that can be larger than the size of the port stack buffer. This is due to the fact that there is no size limitation when identifying the port section between ‘:’ and ‘/’ characters within the callback.
The following SUBSCRIBE request will therefore trigger the overflow:
We confirmed it on our test device with GDB. As we can see below, the program counter of our process got overwritten with ‘AAAA’ (0x41414141):
Gaining a Shell
To fully demonstrate the potential of this vulnerability, we developed a quick proof-of-concept that would land us a reverse shell on the target device. We exploit the stack overflow using the ret2libc technique in order to run an arbitrary command. Given that the size of the command we can run is restricted to 16 characters, we simply launch the UDPServer daemon and exploit the command injection that affects that service to run a longer command that pulls our reverse shell payload over FTP and execute it.

Heap Buffer Overflow via SSDP ST field
The UPnP discovery protocol relies on Simple Service Discovery Protocol (SSDP), a UDP protocol using the HTTP message format.
Two kinds of messages can be sent over SSDP:
M-SEARCH– sent by clients wishing to discover available services on a network.NOTIFY– sent by UPnP servers to announce the establishment or withdrawal of service information to the multicast group.
Handling of SSDP requests is implemented by ProcessSSDPRequest, which only parses M-SEARCH messages and disregards NOTIFY messages.
The origin of the heap buffer overflow lies between lines 43 and 68 where the SSDP handler compares the ST header value to its internal list of exposed service types.
A secure SSDP implementation would only accept an ST header that matches exactly one of its exposed service types (e.g., upnp:rootdevice). In this case, the comparison is made with memcmp – but only up to the length of the currently checked service type. This means that we can pass this check if at least n bytes of our provided ST header value match the service type (e.g. upnp:rootdevicewhateverfollows).
Then, on line 57, the function calls SendSSDPAnnounce2 to reply to our M-SEARCH request with a NOTIFY response using two user controlled inputs: the ST header value (st) and the ST header value length (st_len).
The overflow happens in SendSSDPAnnounce2 on line 23 when calling sprintf to put user controlled data into a 512 bytes buffer allocated on the heap.
We developed the following proof-of-concept with Scapy:
We confirmed it on our test device with GDB. As we can see below, the program counter of our process got messed up due to the presence of invalid values on the heap:
Heap exploitation is always more complex, but the binary provides decent primitives to perform heap spraying. If we want to write a complete PoC we’d have to look at what kind of structures are allocated on the heap at runtime.
Web Management Interface Vulnerabilities (webs, boa)
Summary
Realtek has two different versions of its stock web management interface binary: one is GoAhead-webs (/bin/webs), the other is Boa (/bin/boa).
Each server implements the exact same features, with the exact same vulnerabilities (command injection, overflows). The only difference is that Realtek developers use different APIs to implement their features (e.g., websGetVar to get a query parameter in GoAhead-webs, and req_get_cstream_var in Boa).
In its default state, the interface looks somewhat like this:
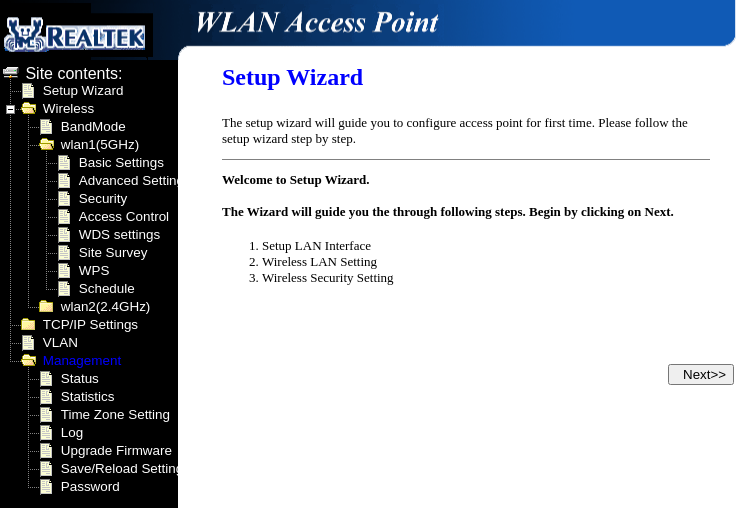
Most vendors and manufacturers use one of these web management binaries but change the appearance of the user interface so that it reflects their brand. During our research, some were found to also remove and/or insert custom features. An obvious example of this is the interface found on an IoT toy tank analyzed by Pentest Partners:

Caveats
The web server is vulnerable to DNS rebinding and does not implement any kind of CSRF protection. This means it could be exploited over the Internet by getting a victim to open an attacker controlled web page and guess the internal IP address running the service.
The binary implements a small authentication feature with a user database saved in a .dat or .txt file depending on the binary (webs or boa). Unless explicitly removed in the code/config by the vendor, a default user account exists (supervisor/supervisor).
Exploitability of identified issues will differ based on what the end vendor/manufacturer did with the Realtek SDK webserver. Some vendors use it as-is, others add their own authentication implementation, some keep all the features from the server, some remove some of them, others insert their own set of features.
However, given that Realtek SDK implementation is full of insecure calls and that (from what we’ve seen so far), developers tends to re-use those examples in their custom code, any binary based on Realtek SDK webserver will probably contain its own set of issues on top of the Realtek ones (if kept).
An excellent example of this is the Edimax webserver implementation that kept vulnerabilities from the Realtek SDK default CGI handlers (e.g., buffer overflow via submit-url parameter), but also copied that exact code into their own custom CGI handlers (see Examination of Edimax home devices – Embedded Lab Vienna for IoT & Security).
Stack Buffer Overflow via formRebootCheck’s submit-url query parameter
A buffer overflow is present in formRebootCheck. The overflow can be triggered by sending an overly long submit-url query parameter:
lastUrl is a static 100 bytes long char array stored in .data section. Given that the variable is above the GOT, we can exploit this vulnerability by overwriting a GOT entry.
A simple demonstration with a 3000 bytes long submit-url value is shown below:
This request will, again, trigger a segfault:
Stack Buffer Overflow via formWsc’s submit-url query parameter
A similar issue is present in formWsc. This overflow can also be triggered by sending an overly long submit-url query parameter:
Again, lastUrl is a static 100 bytes long char array stored in .data section. Given that the variable is above the GOT, we can also overflow exploit this vulnerability by overwriting a GOT entry.
A simple demonstration with a 3000 bytes long submit-url value is shown below:
Yet, another segfault will be triggered:
Stack Buffer Overflow via formWlSiteSurvey’s ifname query parameter
The formWlSiteSurvey form performs an insecure copy from a user controlled buffer into a fixed size variable. WLAN_IF is a static 100 bytes long char array stored in .data section.
We can send the HTTP request below to reach the vulnerable code path:
This will trigger a segfault afterwards, followed by a full reboot:
The full reboot is probably due to an ioctl performed by the webserver that sends a structure holding the IFNAME content to a Realtek kernel driver to get stats from a wireless interface.
Arbitrary Command Execution in formSysCmd
The formSysCmd form is exposing command execution as a feature and is usually reachable via either /goform/formSysCmd or /boafrm/formSysCmd depending on the webserver in use.
We could argue that it’s more of a backdoor rather than a vulnerable endpoint, especially when vendors tend to remove the HTML page represented below from their interface but leave the command execution endpoint enabled.
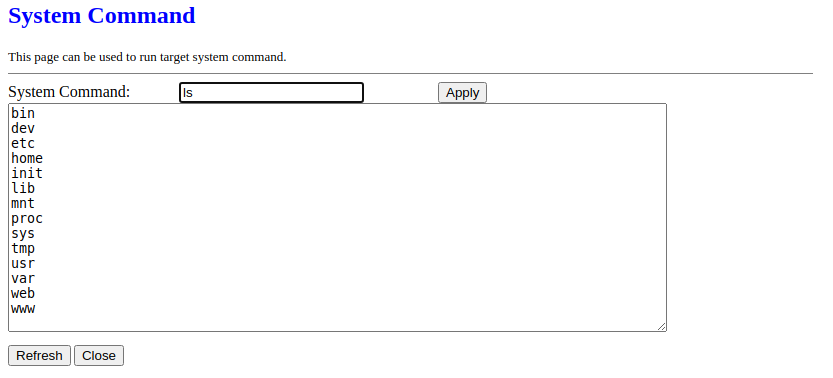
The form code is dead simple: receive a command via the sysCmd query parameter, feed it to system(), and return the results from that command within the next page.
Although probably not required, we’ll reference the HTTP request for completness’ sake:
This “feature” is another great example of what arises with vulnerabilities being distributed down the supply chain. Many testers identified this exact vulnerability in different devices from different vendors but never reported it to Realtek.
A few examples: CVE-2018-20057, CVE-2019-19824, Edimax EW-7438RPn 1.13 – Remote Code Execution.
Command Injection via formWsc’s peerPin query parameter
The formWsc form is vulnerable to arbitrary command injection at multiple locations. All of them are related to a user controlled WPS PIN that is fed to system commands without prior sanitization.
HTTP request to trigger the injection:
Stack Buffer Overflow via formStaticDHCP’s hostname query parameter
The formStaticDHCP form is vulnerable to a stack overflow where a user controlled value (hostname parameter) is insecurely copied to a stack variable using strcpy:
The following HTTP request will trigger the overflow:
Stack Buffer Overflow via formWlanMultipleAP’s submit-url query parameter
The formWlanMultipleAP form is vulnerable to a stack overflow where a user controlled value (submit-url parameter) is insecurely copied to a stack variable using sprintf:
The HTTP request below will trigger the vulnerability:
Stack Buffer Overflow via formWsc’s peerPin query parameter
The formWsc form is vulnerable to a stack overflow where a user controlled value (peerPin parameter) is insecurely copied to a stack variable using sprintf:
The HTTP request below will trigger the overflow:
UDPServer Vulnerabilities
Summary
The following command injection issue found in UDPServer was already identified and reported in 2015 by Peter Adkins, but Mitre never assigned CVEs:
One of the more ‘interesting’ hooks exposed by these devices allow for a ‘UDPServer‘ process to be spawned on the device when called. When started this process listens on the devices LAN IP for data on UDP 9034.
Unfortunately, this process does not appear to perform any sort of input sanitization before passing user input to a system() call. Further investigation finds that the source for this service (UDPServer) is
available in the RealTek SDK, and appears to be a diagnostic tool.
As a result of the above, this process is vulnerable to arbitrary command injection.
By looking at recent samples of the affected binary, we discovered that Realtek released an incomplete fix for this exact issue. We also identified a few buffer overflows.
Caveat
Some devices will launch UDPServer automatically from their init script, some execute it when a specific function in their own code is called (web server request, request to custom network daemon, …), some never execute it and UDPServer is just left as an artifact.
For each identified firmware image with a UDPserver binary, manual analysis is required to confirm if the service is exposed by default or if it can be launched.
Command Injection via UDPServer protocol
When looking at the proof-of-concept and the current code base, it seems that Realtek tried to fix the issues reported in 2015. In 2015 sending \`telnetd -l /bin/sh\` as UDP payload would have triggered the command injection.
Our interpretation is that Realtek tried to fix that by using the following construct we see in the binary:
This does not fix anything given that you can send orf; <injected command>;# and you’ll pass the check while still being able to inject commands.
6 calls to system() are made with user controlled input. Each call follows the same structure as below:
Exploitation
Static Buffer Overflow via UDPServer protocol
On top of command injection, the server is vulnerable to buffer overflows via insecure calls to sprintf (comments added as explaination):
Exploitation won’t be straightforward given that the buffer being overflown will be located in .data section (static declaration).
3 other overflows are present :
Identifying Affected Vendors
To identify devices affected by the vulnerabilities identified in the UPnP/SSDP service, we can rely on Shodan.
After some research, our understanding is that Shodan does this:
- sends SSDP
M-SEARCHto port UDP/1900 to every IP in the whole IPv4 range - for each device that answers with an
SSDP NOTIFY, try to fetch the the device description over UPnP by using theSSDP NOTIFYLocation header (e.g.http://hostname:52881/simplecfg.xml) as target - parse the device description and enrich the host data with it (model name, model number, model description)
The model name, number, and description are exposed by Shodan as the “product” facet. Knowing this, we can fetch all vendors and model names that expose an SSDP/UPnP service over the Internet that is based on the vulnerable Realtek SDK.
We got 198 unique fingerprints for devices that answered over UPnP. If we estimate that each device may have sold 5k copies (on average), the total count of affected devices would be close to a million.
The list of affected devices that we were able to identify can be found in the appendix.
Realtek System Indicators
If you are assessing an embedded device, these are indicators of a system relying on Realtek’s SDK.
An easy indicator is the /etc/motd file mentioning rlx-linux:
Hostname is usually set to rlx-linux in the init script:
Another is /etc/version, which is not always present:
rlx-linux is a stripped down Linux system from Realtek, built specifically for the RTL chipsets.
Timeline
- 2021-05-17 – Ask Realtek security team for a way to send our report securely.
- 2021-05-18 – Realtek security team provides their PGP key, we send encrypted advisories.
- 2021-05-25 – Realtek security team request Python PoC scripts.
- 2021-05-25 – We provide scripts for every reported vulnerability.
- 2021-06-10 – Realtek security team provides us the patched code, along with a patched firmware for the 96D_92D demo boards.
- 2021-06-10 – We review the patch and send our comments related to checks that could still be bypassed.
- 2021-06-11 – Realtek security team provides us with the exact list of affected versions for “Jungle” and “Luna” SDKs. The 2.x branch is no longer supported by Realtek, being 11 years old.
- 2021-06-16 – We request CVE identifiers from MITRE.
- 2021-08-05 – We receive CVE identifiers from MITRE.
- 2021-08-13 – Realtek publish its advisory.
- 2021-08-16 – End of 90 days disclosure window, releasing this post.
About Onekey
ONEKEY is the leading European specialist in Product Cybersecurity & Compliance Management and part of the investment portfolio of PricewaterhouseCoopers Germany (PwC). The unique combination of the automated ONEKEY Product Cybersecurity & Compliance Platform (OCP) with expert knowledge and consulting services provides fast and comprehensive analysis, support, and management to improve product cybersecurity and compliance from product purchasing, design, development, production to end-of-life.

CONTACT:
Sara Fortmann
Senior Marketing Manager
sara.fortmann@onekey.com
euromarcom public relations GmbH
team@euromarcom.de
RELATED RESEARCH ARTICLES

How We Taught Our Platform to Understand RTOS Firmware
Discover how ONEKEY’s platform breaks open real-time operating system (RTOS) firmware. Learn how automated architecture detection, load address recovery, and component identification bring transparency and security to embedded devices in automotive, medical, and industrial sectors.
Ready to automate your Product Cybersecurity & Compliance?
Make cybersecurity and compliance efficient and effective with ONEKEY.


