Transform Incident Response Into Proactive Security
Incident response doesn’t have to mean constant firefighting. With ONEKEY, PSIRTs detect vulnerabilities in deployed products, validate exploitability instantly. Teams gain the clarity and speed to move from reactive fixes to proactive, lifecycle-wide product security.

Industry Leaders Rely on ONEKEY
.png)
.png)
.png)



























.png)
.png)
.png)



























.png)
.png)
.png)



























From Firefighting to Proactive PSIRT
ONEKEY supports every maturity level – helping teams respond faster today and build proactive processes for tomorrow.
Excessive False Positives Without Context
PSIRT teams are overwhelmed by endless vulnerability alerts from deployed products. Most tools flag every CVE tied to firmware components without checking if it’s exploitable in context. Alert fatigue, wasted time, and lost focus on what truly matters. Without context – whether a component is used, reachable, or even compiled – teams can’t triage effectively. Noise grows, pressure mounts, and real risks slip through while time is spent on non-impactful alerts.
Manual Impact Assessment Slows Response
Once a vulnerability is found, PSIRT teams must assess its impact across all firmware variants — a process that’s often slow and manual. Each package can differ in configuration, libraries, or build environments, forcing teams to analyze every binary individually. Without centralized visibility, impact analysis drags on, products stay exposed longer, and delays in patching, escalation, or communication increase the risk of reputational and financial damage.
No Visibility into Firmware Components
In many embedded systems, PSIRT teams lack full visibility into the components inside deployed firmware. Without a clear SBOM, it’s nearly impossible to know which open-source libraries, proprietary modules, or vendor packages are in use – creating a major blind spot in product security. When an incident occurs, teams can’t quickly answer what’s present or affected, leading to uncertainty, delay, and reactive communication instead of confident, evidence-based response.
Smart Features for Confident Incident Response
Automated Firmware Vulnerability Evaluation
When new vulnerabilities are disclosed, PSIRT teams need to know fast if their products are affected. ONEKEY’s Auto Impact Assessment removes the guesswork by analyzing each vulnerability in the real firmware context — no source code required. It reveals whether a vulnerability is exploitable, mitigated, or irrelevant, helping teams focus on actionable issues, speed up triage, and communicate with confidence.

SBOM Management for Faster Incident Response
When a new vulnerability is disclosed, PSIRT teams must quickly answer one question: Which products are affected? ONEKEY’s SBOM Management delivers full visibility into every component of deployed firmware – even without source code. By generating precise SBOMs directly from binaries, ONEKEY helps teams instantly identify impacted components, third-party libraries, and vendor packages.
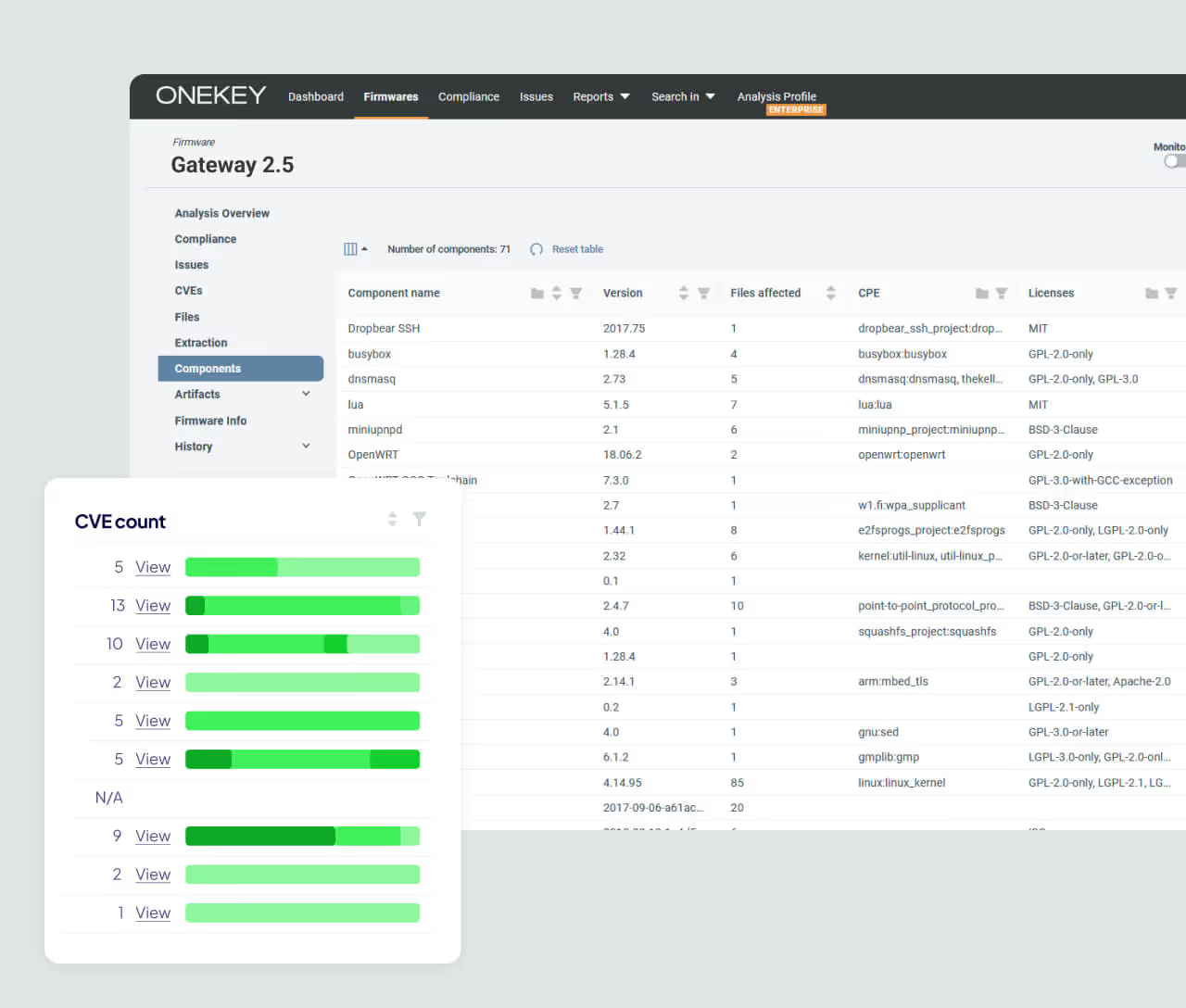
Export-Ready PSIRT Reporting
ONEKEY gives PSIRT teams powerful, export-ready reporting to speed up response and simplify communication. The platform generates incident and vulnerability reports in formats like PDF, SPDX, CycloneDX, and JSON, making it easy to share findings with teams, customers, or regulators. With built-in VEX and VDR support, ONEKEY clearly separates exploitable from non-exploitable issues, reduces triage effort, and adds full traceability across the product lifecycle.
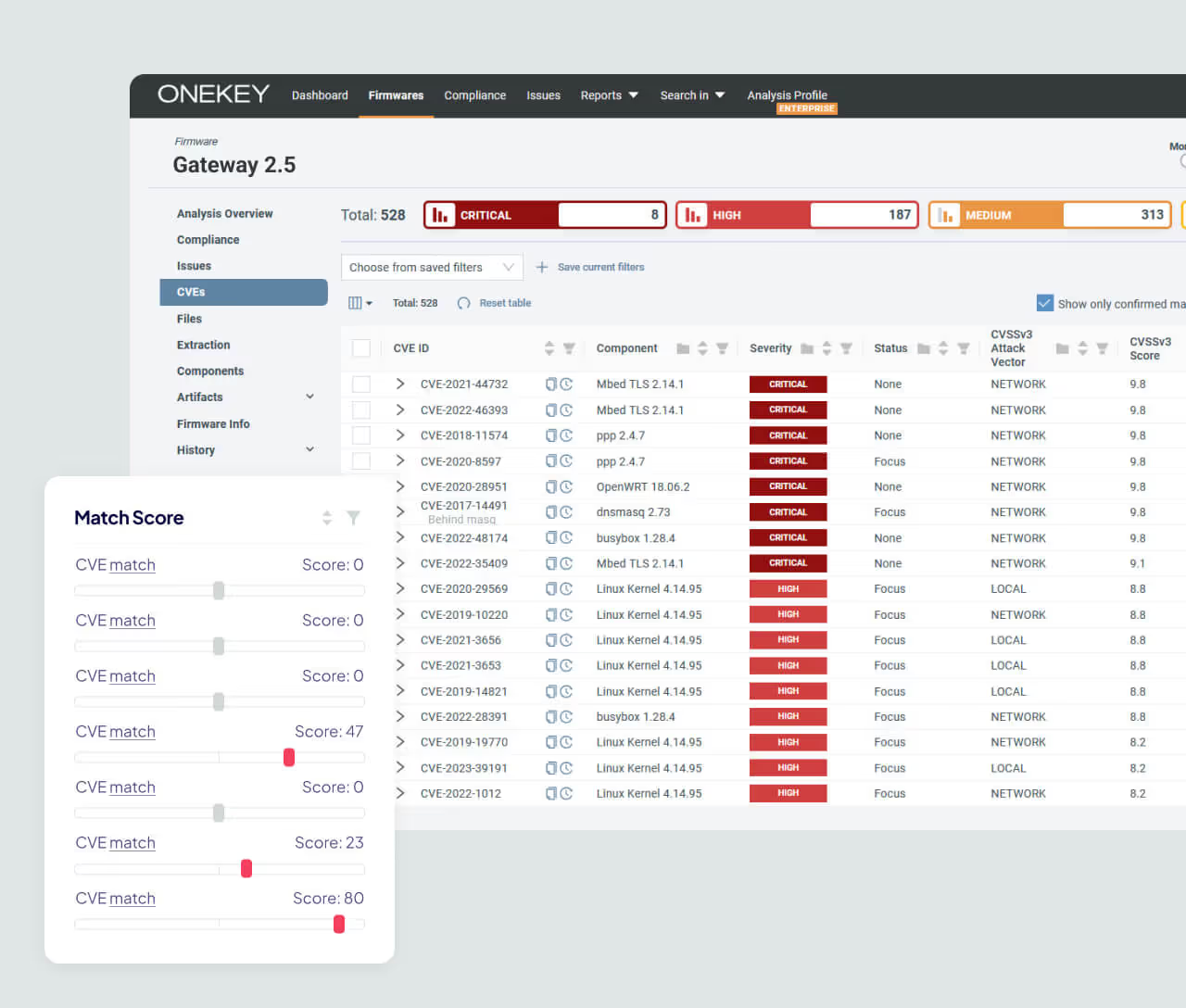
Why ONEKEY Transforms Incident Response
ONEKEY automates detection, impact assessment, and reporting – helping PSIRT teams respond faster, communicate clearly, and stay in control.
Accelerate Vulnerability Identification Across Products and Firmware
In incident response, time is everything. When a new vulnerability appears, PSIRT teams need to know fast which firmware versions and product lines are affected. Without full visibility, manual analysis can take days. ONEKEY changes that by analyzing binaries directly and generating precise SBOMs with complete component and version data – helping teams pinpoint affected products in minutes and accelerate triage and containment.
Eliminate Noise with Context-Aware Impact Assessment
PSIRT teams face endless vulnerability lists without context. In embedded systems, not every issue is exploitable – reacting to all of them wastes time and resources. ONEKEY’s automated impact assessment analyzes each firmware build in its real runtime context, cutting false positives by over 60% and helping teams focus only on what truly matters.
Streamline PSIRT Reporting for Customers and Stakeholders
Clear communication during a security incident is essential – with engineers, executives, customers, and regulators alike. ONEKEY streamlines this process with structured, professional incident reports in PDF, JSON, CycloneDX, or VEX. PSIRT teams can show what’s affected, what’s not, and what’s being done – building trust and proving accountability with reports ready in just a few clicks.
FACTS & Figures
FACTS & Figures
Up to 80% Reduction in Triage and Justification Time
Up to 10x Faster Detection and Reporting
350% Boost in PSIRT Team Productivity and Satisfaction
Turn Complex Incidents into Clear Communication
With ONEKEY, PSIRT teams translate technical findings into ready-to-share reports for customers, partners, and regulators – instantly and confidently.
Why Customers Trust Us
Incident Response. Managed with Confidence.
Leverage automation and clarity to handle vulnerabilities faster, smarter, and with complete transparency.

Respond Fast to Critical Threats
Identify critical vulnerabilities with ONEKEY's automated zero-day analysis. Improve response time for IoT/OT with precise, centralized monitoring.

Tailor Your Threat Models
Automatically standardize component names across SBOMs – eliminate inconsistencies, simplify cross-version tracking, and improve accuracy and security in component management.

Ensure Security with Continuous Scans
ONEKEY re-analyzes your firmware daily, updating vulnerabilities and providing alerts to keep your firmware secure.
FAQs
Get detailed answers to the most common questions on safeguarding your connected products.

What is Product Cybersecurity?
Product cybersecurity ensures your digital products—whether software, hardware, or connected devices—are protected against cyber threats throughout their entire lifecycle. From design to deployment and beyond, robust cybersecurity practices safeguard against data breaches, unauthorized access, and cyberattacks. This proactive approach not only secures the product but also ensures compliance with evolving regulations, reducing risks and maintaining the integrity and trustworthiness of your technology.
Why is Product Cybersecurity Important?
Product cybersecurity is essential to protect your digital products from cyber threats, safeguarding sensitive data and ensuring seamless operation. Without it, your products and users are at risk of attacks, data breaches, and unauthorized access that can result in costly financial losses, reputational damage, and compromised safety. Strong cybersecurity practices help you stay compliant with regulations, build customer trust, and keep your products resilient against evolving cyber threats.
How do you ensure product cybersecurity?
Securing your products requires a strategic and continuous approach throughout their entire lifecycle. Here’s how you can achieve it:
- Conduct Security Audits & Assessments: Regularly evaluate your products to uncover and fix vulnerabilities before they become threats.
- Manage Vulnerabilities Effectively: Leverage SBOMs, VEX, and automated tools to track, assess, and mitigate risks.
- Stay Updated: Keep your products secure by applying patches and updates to defend against the latest cyber threats.
- Ensure Compliance: Meet all relevant security standards and regulations to avoid legal risks and maintain customer trust.
Build. Comply. Resist. Repeat. With these steps, you’ll stay ahead of the curve and keep your products and customers secure.
What is an SBOM used for?
An SBOM (Software Bill of Materials) gives you a complete overview of all components in your software. It’s key for managing vulnerabilities, sharing information, ensuring license compliance, and maintaining transparency across your supply chain. With an SBOM, you gain the visibility you need to keep your products secure and compliant—every step of the way.
What is a Digital Cyber Twin?
A Digital Cyber Twin is a virtual replica of your product’s digital ecosystem. It lets you test and analyze your system in a safe, simulated environment—detecting vulnerabilities and optimizing security before they can impact your real-world product. It’s like having a crystal ball for your cybersecurity, helping you stay ahead of potential threats without risking your actual systems.







